In these article series, I am going to swap my Windows 2012 R2 Domain Controllers with Windows Server 2019 without interrupting critical IT services. While doing this, I want to keep using the same IP addresses and computer names which I am currently using on Windows 2012 R2 Domain Controllers. This article assumes you have 2 Domain Controllers in your Domain.
- Make sure you patch the latest updates on your existing Domain Controllers first.
- If there are any services that you need to move to another server, make sure you do it now. AD Certificate Authority Role is sometines installed Domain Controllers by system admins. Here is an article that explains how to move esxiting CA to another server.
- You can check supported Server OS for Forest and Domain Functional Levels from the link below. My current functional levels are 2008 R2 for both Forest and Domain. I don't have to raise Functional Levels on my DCs.
https://docs.microsoft.com/en-us/windows-server/identity/ad-ds/active-directory-functional-levels
- Create 2 new Windows Server 2019 and patch the servers with the latest updates. Srv03 and Srv04 is not Domain Members yet and No IP configuration is done yet.

-Check which DC holds the FSMO Roles by using "netdom query fsmo" command. I need to check this to make sure that I am not demoting the dc which holds the FSMO roles.
- Ensure AD replication is working: The DFSR migration depends entirely on each domain controller receiving and sending state changes via AD replication. You can download and use Active Directory Replication Status Tool to analyze the replication status for domain controllers in an Active Directory domain or forest. If this tool finds any errors, first fix those errors and DO NOT continue for the migration.
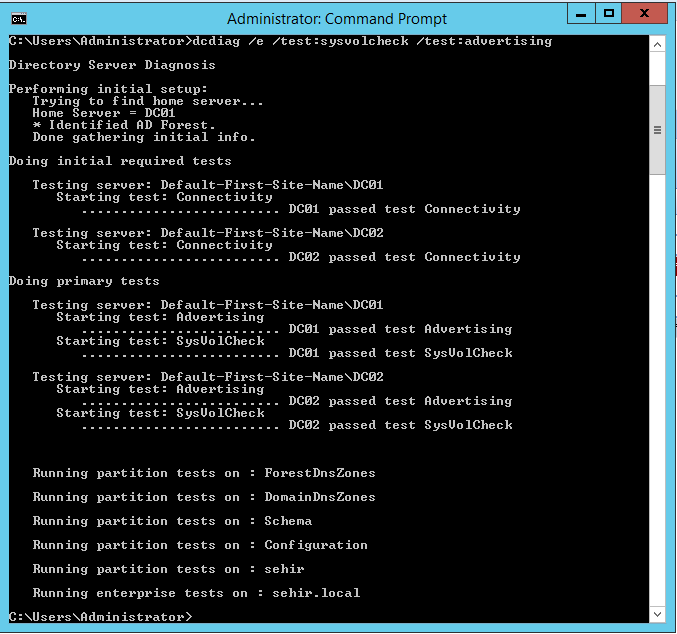
Make sure all your domain controllers are passing the connectivity, SYSVOL, and advertising tests with no errors like below.
dcdiag /e /test:sysvolcheck /test:advertising
DEMOTING THE SECONDARY DC:
- Demote the secondary DC (DC02) which does not hold the FSMO roles.
Open Server Manager > Manage > Remove Roles and Features> Next > Next > Uncheck Active Directory Domain Services
Click Remove Features button in the pop-up window
Click Demote this domain Controller option
DO NOT select Force option. Click Next
DNS and Global Catalog roles will be removed, select Proceed with Removal checkbox, click Next
This server will disjoin the domain at the end of this demotion process. Therefore we specify a local admistrator password on this screen.
Click Demote button
DC02 succesfully demoted.
MetaData CleanUp:
Logon to DC01 and open Active Directory Sites and Services. You will see the demoted server is still listed there. Right click and Delete.
On DC01 do the following:
Open Active Directory Users and Computers> Go into the “Domain Controllers” OU and verify the Computer Object is removed.
Open Active Directory Users and Computers> Go into the “Computers” OU and delete DC02 Computer object.
Open DNS Management. Reverse DNS record might be still there, Delete DC02 DNS record if it is still there
Open DNS Management. Check if Forest DNSZones and Domain DNS Zones, if there is a record for DC02, delete it. Check every single folder in DNS and make sure there is no remaining record or enrty that belongs to the old, demoted server.
In Part2, We will Promote the Srv04 as the secondary DC.